Cybersecurity
Protection at the highest level
With our specialized expertise in information security, we chart a safe course for your project plans right from the very start, ensuring that your company stays firmly on track at all times. We are the ideal partner for all your security needs, from initial idea to operational deployment; these needs are considered right from the agile development stage.
Protect yourself from the increasing daily threats
Cyberattacks such as ransomware and phishing, as well as data breaches and leaks, shake the trust in the digital world almost daily. Globally, there are 580 password attacks per second, and the Federal Office for Cyber Security receives up to 350 attack and threat reports per day. In our holistic approach, we integrate all aspects of cybersecurity and offer protection from a single source with high user-friendliness.
Precision Security
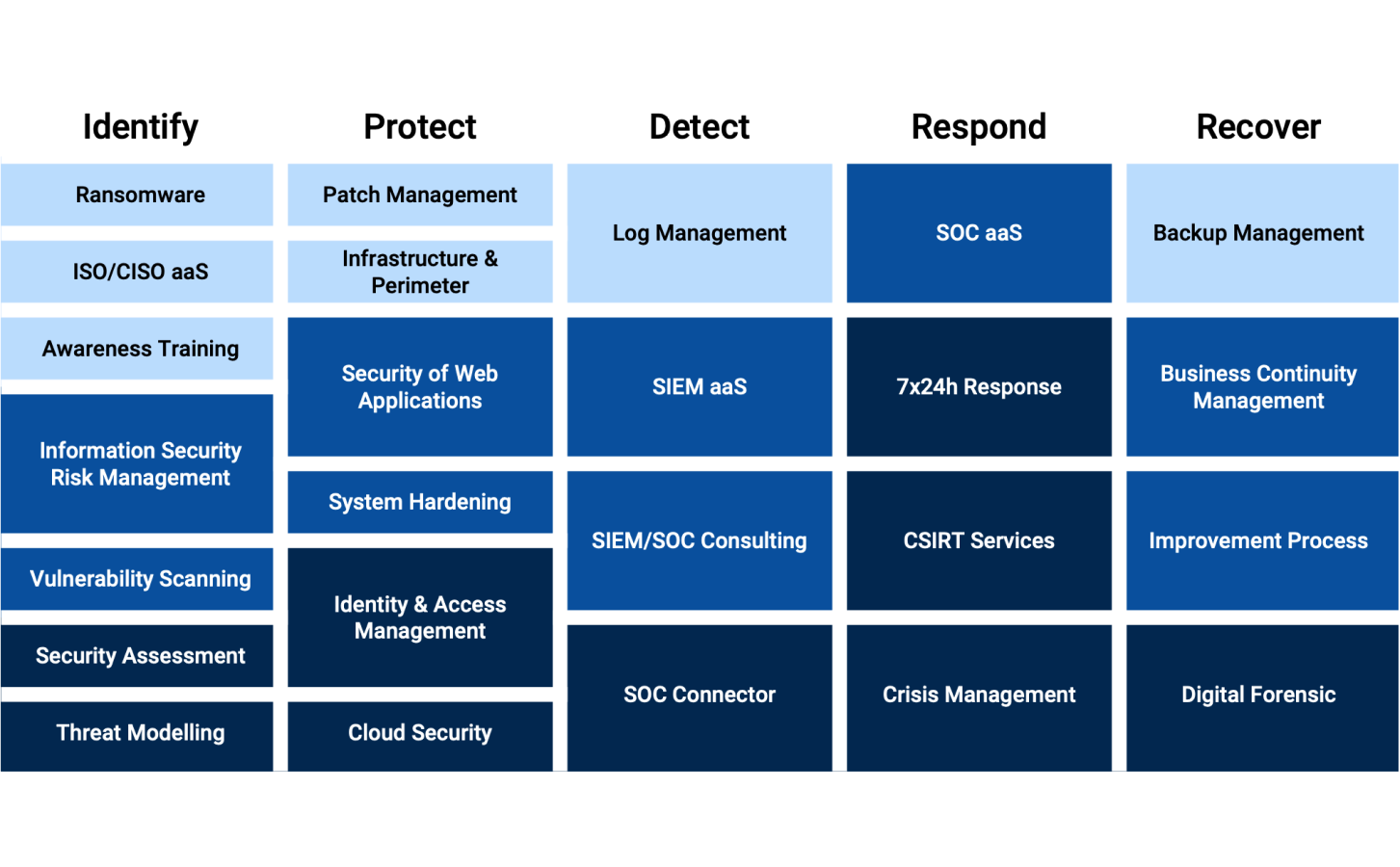
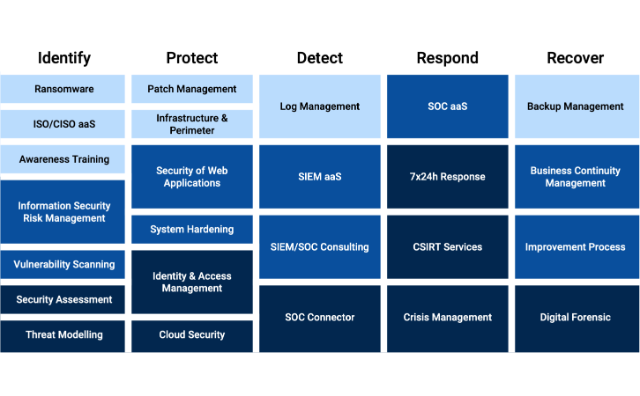
With our three security service packages, we offer optimal protection for every security need:
Basic Advanced High Secure
Download the new ti&m special "Digital Trust" for free now.